- enables proxy compatibility on startup
- Improved CSRF protection
- working with session after
2.176.2since SECURITY-626
enables proxy compatibility on startup
-Djenkins.model.Jenkins.crumbIssuerProxyCompatibility=true
- temporary settings in Script:
System.setProperty('jenkins.model.Jenkins.crumbIssuerProxyCompatibility', 'true') System.getProperty('jenkins.model.Jenkins.crumbIssuerProxyCompatibility')
change in Configure Global Security
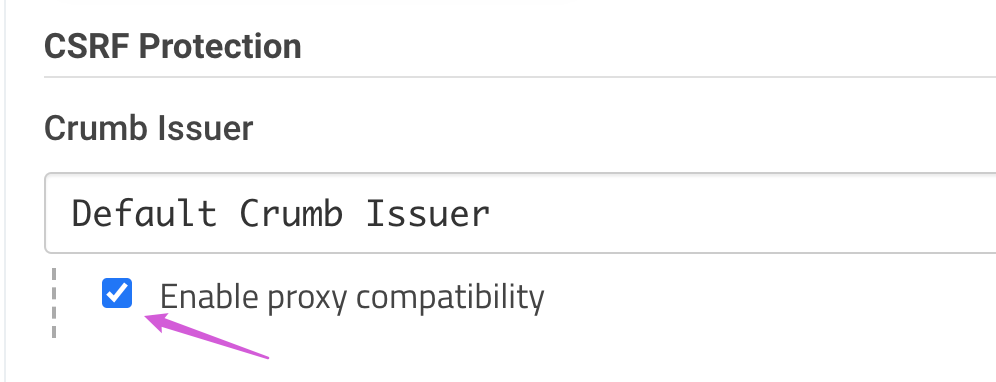
Improved CSRF protection
Upgrading to Jenkins 2.176.2
- SECURITY-626
- CSRF
/
tokens (crumbs) are now only valid for the web session they were created in to limit the impact of attackers obtaining them. Scripts that obtain a crumb using the
/crumbIssuer/apiURL will now fail to perform actions protected from CSRF unless the scripts retain the web session ID in subsequent requests.- CSRF Protection Explained
Scripts could instead use an API token, which has not required a CSRF token (crumb)
since Jenkins 2.96.
working with session after 2.176.2 since SECURITY-626
references:
via curl
[!TIP] check cookie
$ cat ${COOKIEJAR} # Netscape HTTP Cookie File # https://curl.se/docs/http-cookies.html # This file was generated by libcurl! Edit at your own risk. #HttpOnly_jenkins.marslo.com.com FALSE / TRUE 0 JSESSIONID.a054fd7a node015xsx4fybmo2k1oxpjg5f2dzw4265.node0
SERVER="http://localhost:8080"
# File where web session cookie is saved
COOKIEJAR="$(mktemp)"
CRUMB=$(curl -u "admin:admin" \
--cookie-jar "$COOKIEJAR" \
"$SERVER/crumbIssuer/api/xml?xpath=concat(//crumbRequestField,%22:%22,//crumb)" \
)
curl -X POST \
-u "admin:admin" \
--cookie "$COOKIEJAR" \
-H "$CRUMB" \
"$SERVER"/job/someJob/build
via wget
SERVER="http://localhost:8080"
# File where web session cookie is saved
COOKIEJAR="$(mktemp)"
CRUMB="$(wget --user=admin \
--password=admin \
--auth-no-challenge \
--save-cookies "$COOKIEJAR" \
--keep-session-cookies \
-q \
--output-document \
- \
"$SERVER/crumbIssuer/api/xml?xpath=concat(//crumbRequestField,%22:%22,//crumb)"
)"
wget --user=admin \
--password=admin \
--auth-no-challenge \
--load-cookies "$COOKIEJAR" \
--header="$CRUMB" \
--post-data="" \
-q \
"$SERVER"/job/someJob/build
example
with crumb only
will get issue
403: No valid crumb was included in the request$ curl -H ${crumb} \ -X POST \ https://jenkins.marslo.com/safeRestart <html> <head> <meta http-equiv="Content-Type" content="text/html;charset=utf-8"/> <title>Error 403 No valid crumb was included in the request</title> </head> <body><h2>HTTP ERROR 403 No valid crumb was included in the request</h2> <table> <tr><th>URI:</th><td>/safeRestart</td></tr> <tr><th>STATUS:</th><td>403</td></tr> <tr><th>MESSAGE:</th><td>No valid crumb was included in the request</td></tr> <tr><th>SERVLET:</th><td>Stapler</td></tr> </table> <hr><a href="https://eclipse.org/jetty">Powered by Jetty:// 9.4.39.v20210325</a><hr/> </body> </html>with crumb and cookie
$ COOKIEJAR="$(mktemp)" $ CRUMB="$(curl -s \ --cookie-jar "${COOKIEJAR}" \ "https://jenkins.marslo.com/crumbIssuer/api/json" | jq -r '.crumbRequestField + ":" + .crumb' )" $ curl -v \ -X POST \ --cookie "${COOKIEJAR}" \ -H "${CRUMB}" \ https://jenkins.marslo.com/safeRestart ... * Connection state changed (MAX_CONCURRENT_STREAMS == 250)! < HTTP/2 302 < date: Wed, 09 Jun 2021 15:25:14 GMT < location: https://jenkins.marslo.com/ < server: Jetty(9.4.39.v20210325) < vary: Accept-Encoding < x-content-type-options: nosniff < content-length: 0 < * Connection #0 to host jenkins.marslo.com left intact
To disable this improvement you can set the system property
via
JAVA_OPTS-Dhudson.security.csrf.DefaultCrumbIssuer.EXCLUDE_SESSION_ID=truetemporary settings in Script:
- example for SECURITY-626
System.setProperty('hudson.security.csrf.DefaultCrumbIssuer.EXCLUDE_SESSION_ID', 'true') System.getProperty('hudson.security.csrf.DefaultCrumbIssuer.EXCLUDE_SESSION_ID')
via plugin Strict Crumb Issuer
get crumberIssuer with script
import org.jenkinsci.plugins.strictcrumbissuer.StrictCrumbIssuer
StrictCrumbIssuer issuer = jenkins.model.Jenkins.instance.crumbIssuer
String jenkinsCrumb = "${issuer.crumbRequestField}:${issuer.crumb}"
println jenkinsCrumb