- Core design principles
- ports and protocols
- architecture
- jsonpath
- options
- kubectl alias
- token
- tear down
[!TIP]
kubernetes.ioadd/_printas suffix in the url, it will show pages into one page i.e.:
reference
- * Play with Kubernetes
- * Glossary
- * Install Kubernetes Cluster on Centos 8 With Kubeadm and CRI-O
- * 在 CentOS 上部署 Kubernetes 集群
- * Kubernetes 中文指南/云原生应用架构实战手册
- * Create static Pods
- * Implementation details
- * Scheduling, Preemption and Eviction
- * Resource Management for Pods and Containers
- * Administer a Cluster
- * Kubernetes概念辨析
- * Step by step installation of 3-nodes Kubernetes Cluster on CentOS 8
- * KUBERNETES INSTALLATION ON CENTOS 8
- * Reference > Configuration APIs
- KUBERNETES: AN OVERVIEW
- What Is Kubernetes: A Container Orchestration Platform
- KUBERNETES, OPEN-SOURCE CONTAINER ORCHESTRATION TECHNOLOGY
- Boosting your kubectl productivity
- 23 Advanced kubectl commands
- 8 Kubernetes Tips and Tricks
- Linux namespace简介
- Well-Known Labels, Annotations and Taints
- * best practices
- 12 Kubernetes Configuration Best Practices
- Best Kubernetes Certifications for 2023 [Ranked]
- Important Kubernetes Cluster Configurations
- Kubernetes Architecture
- * How to Access Kubernetes API Server
- Kubernetes(k8s)基础概念介绍
- Migrating a cluster from flannel to Calico
resources:
- Free Kubernetes Ebook: Kubernetes up and running
- How to Learn Kubernetes (Complete Roadmap & Resources)
- kelseyhightower/kubernetes-the-hard-way
- * Kubernetes Tutorials For Beginners: 43 Comprehensive Guides
- * How to Setup Jenkins Build Agents on Kubernetes Pods
- Kubernetes Learning Resources
- Kubernetes Documentation/Tasks
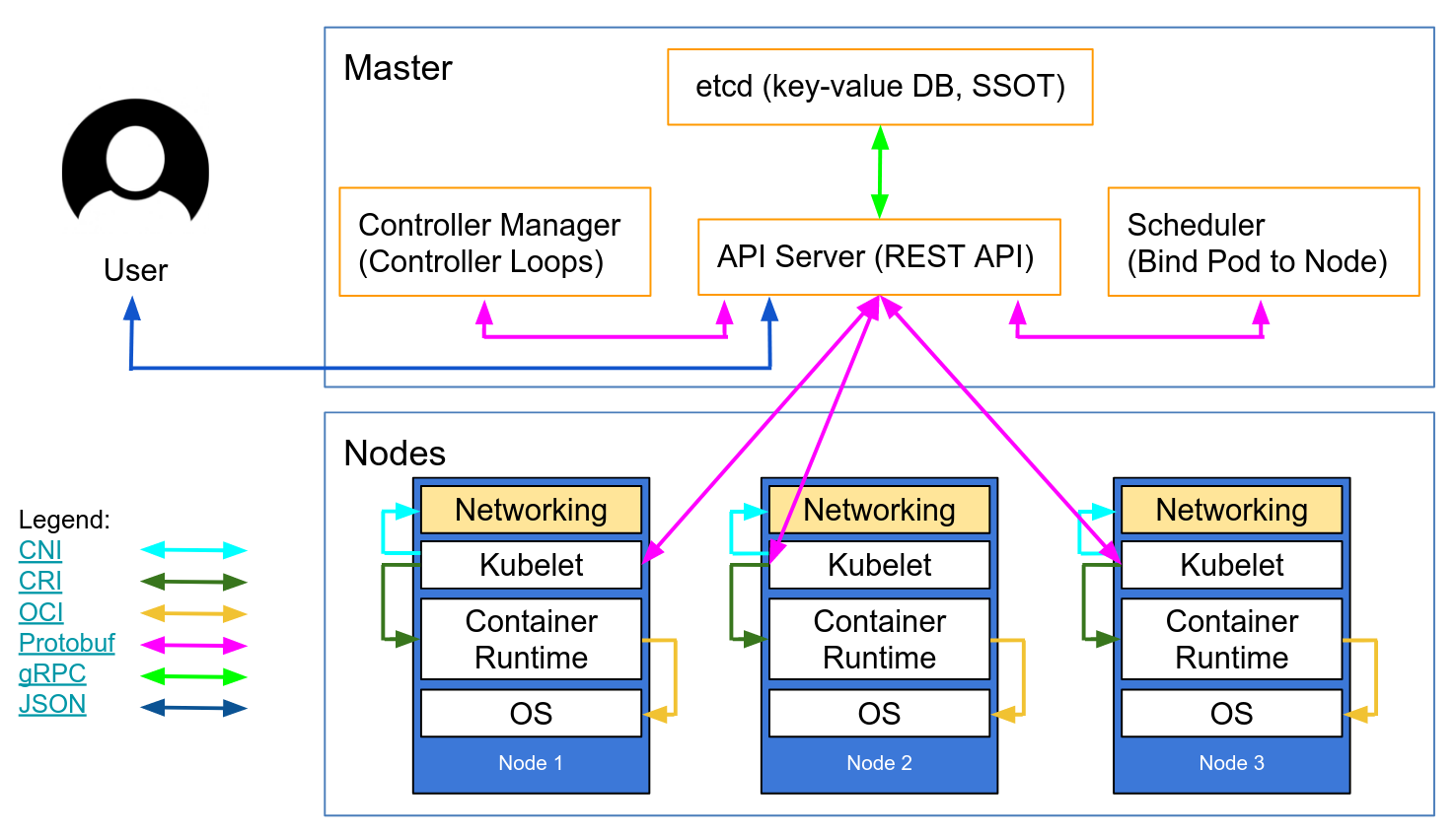
Core design principles
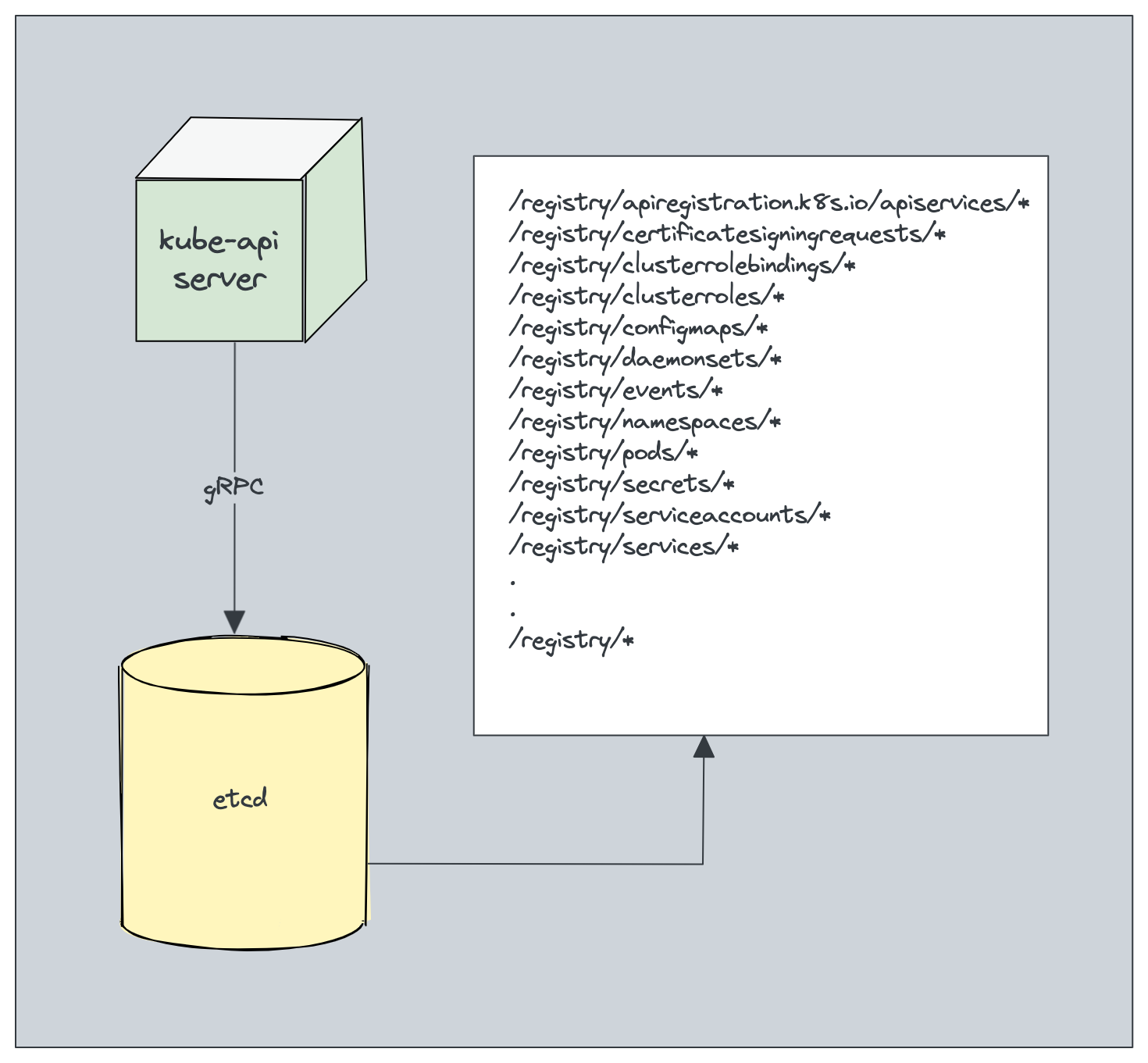
Constants and well-known values and paths
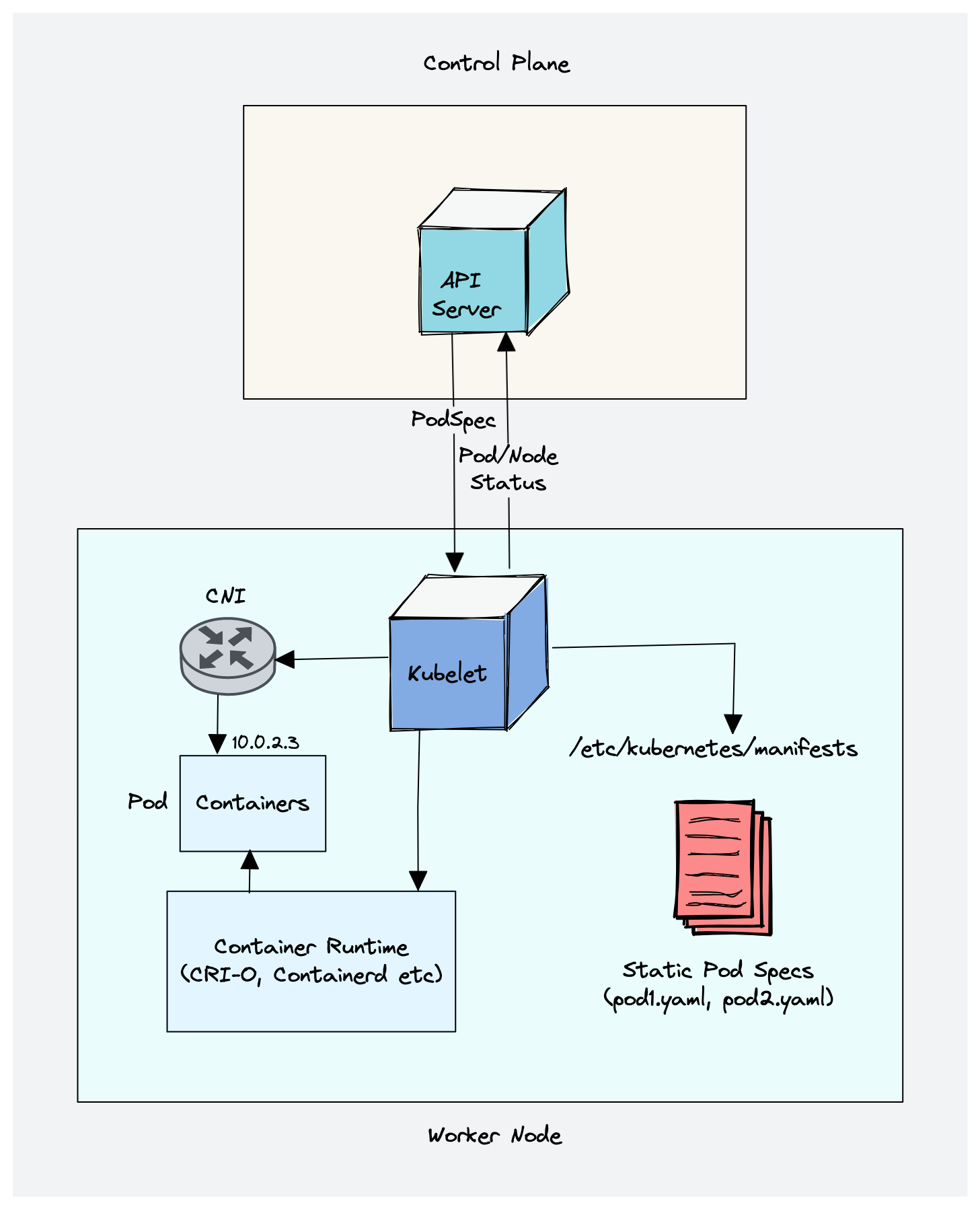
/etc/kubernetes/manifests
[!TIP]
/etc/kubernetes/manifestsas the path where kubelet should look for static Pod manifests. Names of static Pod manifests are:
etcd.yamlkube-apiserver.yamlkube-controller-manager.yamlkube-scheduler.yaml
/etc/kubernetes
[!TIP]
- Important Kubernetes Cluster Configurations
/etc/kubernetes/as the path where kubeconfig files with identities for control plane components are stored. Names of kubeconfig files are:kubelet.conf(bootstrap-kubelet.conf during TLS bootstrap)controller-manager.confscheduler.confadmin.conffor the cluster admin and kubeadm itself
names of certificates and key files
[!TIP]
ca.crt,ca.keyfor the Kubernetes certificate authorityapiserver.crt,apiserver.keyfor the API server certificateapiserver-kubelet-client.crt,apiserver-kubelet-client.keyfor the client certificate used by the API server to connect to the kubelets securelysa.pub,sa.keyfor the key used by the controller manager when signing ServiceAccountfront-proxy-ca.crt,front-proxy-ca.keyfor the front proxy certificate authorityfront-proxy-client.crt,front-proxy-client.keyfor the front proxy client
API server
static Pod manifest
[!TIP]
apiserver-advertise-addressandapiserver-bind-portto bind to; if not provided, those value defaults to the IP address of the default network interface on the machine and port6443service-cluster-ip-rangeto use for services- If an external etcd server is specified, the
etcd-serversaddress and related TLS settings (etcd-cafile,etcd-certfile,etcd-keyfile);
- if an external etcd server is not be provided, a local etcd will be used ( via host network )
- If a cloud provider is specified, the corresponding
--cloud-provideris configured, together with the--cloud-configpath if such file exists (this is experimental, alpha and will be removed in a future version)
other api server flags
--insecure-port=0to avoid insecure connections to the api server--enable-bootstrap-token-auth=trueto enable the BootstrapTokenAuthenticator authentication module. See TLS Bootstrapping for more details--allow-privilegedto true (required e.g. by kube proxy)--requestheader-client-ca-fileto front-proxy-ca.crt--enable-admission-pluginsto:NamespaceLifecyclee.g. to avoid deletion of system reserved namespacesLimitRangerandResourceQuotato enforce limits on namespacesServiceAccountto enforce service account automationPersistentVolumeLabelattaches region or zone labels to PersistentVolumes as defined by the cloud provider (This admission controller is deprecated and will be removed in a future version. It is not deployed by kubeadm by default with v1.9 onwards when not explicitly opting into using gce or aws as cloud providers)DefaultStorageClassto enforce default storage class on PersistentVolumeClaim objectsDefaultTolerationSecondsNodeRestrictionto limit what a kubelet can modify (e.g. only pods on this node)
--kubelet-preferred-address-typestoInternalIP,ExternalIP,Hostname; this makeskubectl logsand other API server-kubelet communication work in environments where the hostnames of the nodes aren't resolvable- Flags for using certificates generated in previous steps:
--client-ca-filetoca.crt--tls-cert-filetoapiserver.crt--tls-private-key-filetoapiserver.key--kubelet-client-certificatetoapiserver-kubelet-client.crt--kubelet-client-keytoapiserver-kubelet-client.key--service-account-key-filetosa.pub--requestheader-client-ca-filetofront-proxy-ca.crt--proxy-client-cert-filetofront-proxy-client.crt--proxy-client-key-filetofront-proxy-client.key
- Other flags for securing the front proxy (API Aggregation) communications:
--requestheader-username-headers=X-Remote-User--requestheader-group-headers=X-Remote-Group--requestheader-extra-headers-prefix=X-Remote-Extra---requestheader-allowed-names=front-proxy-client
controller manager
static Pod manifest
[!TIP]
- If kubeadm is invoked specifying a
--pod-network-cidr, the subnet manager feature required for some CNI network plugins is enabled by setting:
--allocate-node-cidrs=true--cluster-cidrand--node-cidr-mask-sizeflags according to the given CIDR- If a cloud provider is specified, the corresponding
--cloud-provideris specified, together with the--cloud-configpath if such configuration file exists (this is experimental, alpha and will be removed in a future version)
other flags
--controllersenabling all the default controllers plusBootstrapSignerandTokenCleanercontrollers for TLS bootstrap. See TLS Bootstrapping for more details--use-service-account-credentialsto true- Flags for using certificates generated in previous steps:
--root-ca-fileto ca.crt--cluster-signing-cert-filetoca.crt, if External CA mode is disabled, otherwise to""--cluster-signing-key-filetoca.key, if External CA mode is disabled, otherwise to""--service-account-private-key-fileto sa.key
ports and protocols
contol plane
| PROTOCOL | DIRECTION | PORT RANGE | PURPOSE | USED BY |
|---|---|---|---|---|
| TCP | Inbound | 6443 |
Kubernetes API server | All |
| TCP | Inbound | 2379-2380 |
etcd server client API | kube-apiserver, etcd |
| TCP | Inbound | 10250 |
Kubelet API | Self, Control plane |
| TCP | Inbound | 10259 |
kube-scheduler | Self |
| TCP | Inbound | 10257 |
kube-controller-manager | Self |
worker node(s)
| PROTOCOL | DIRECTION | PORT RANGE | PURPOSE | USED BY |
|---|---|---|---|---|
| TCP | Inbound | 10250 |
Kubelet API | Self, Control plane |
| TCP | Inbound | 30000-32767 |
NodePort Services | All |
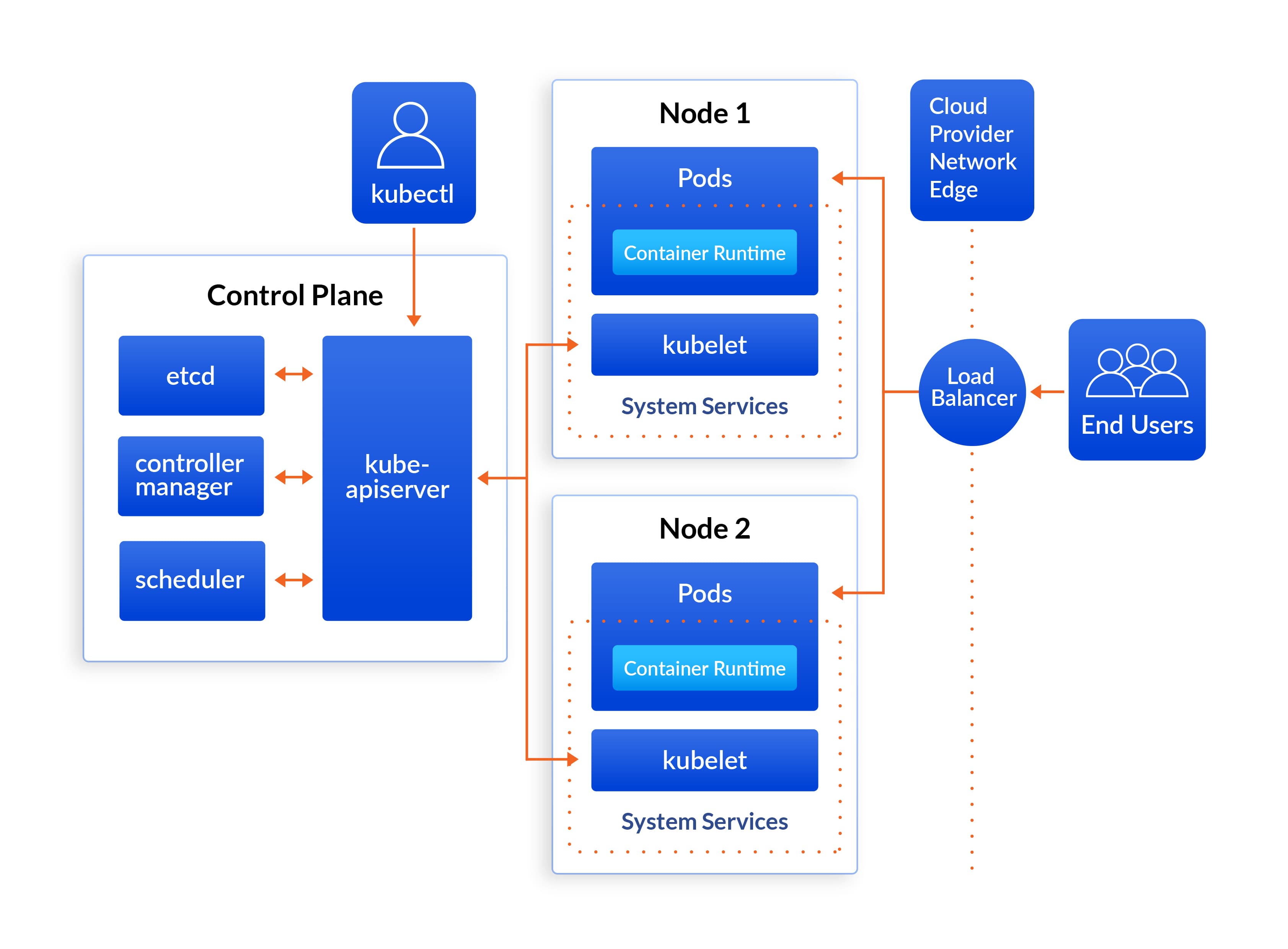
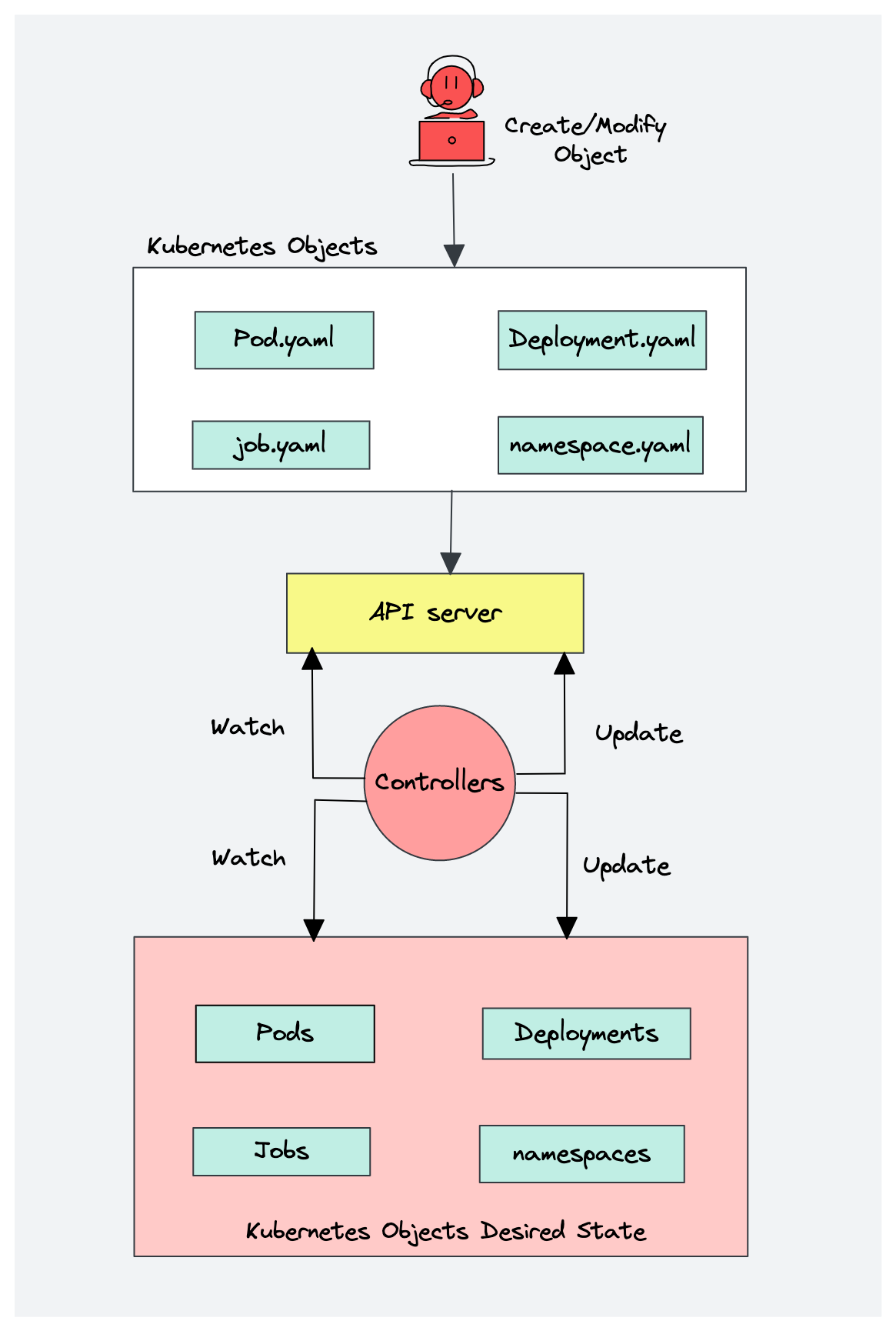
architecture
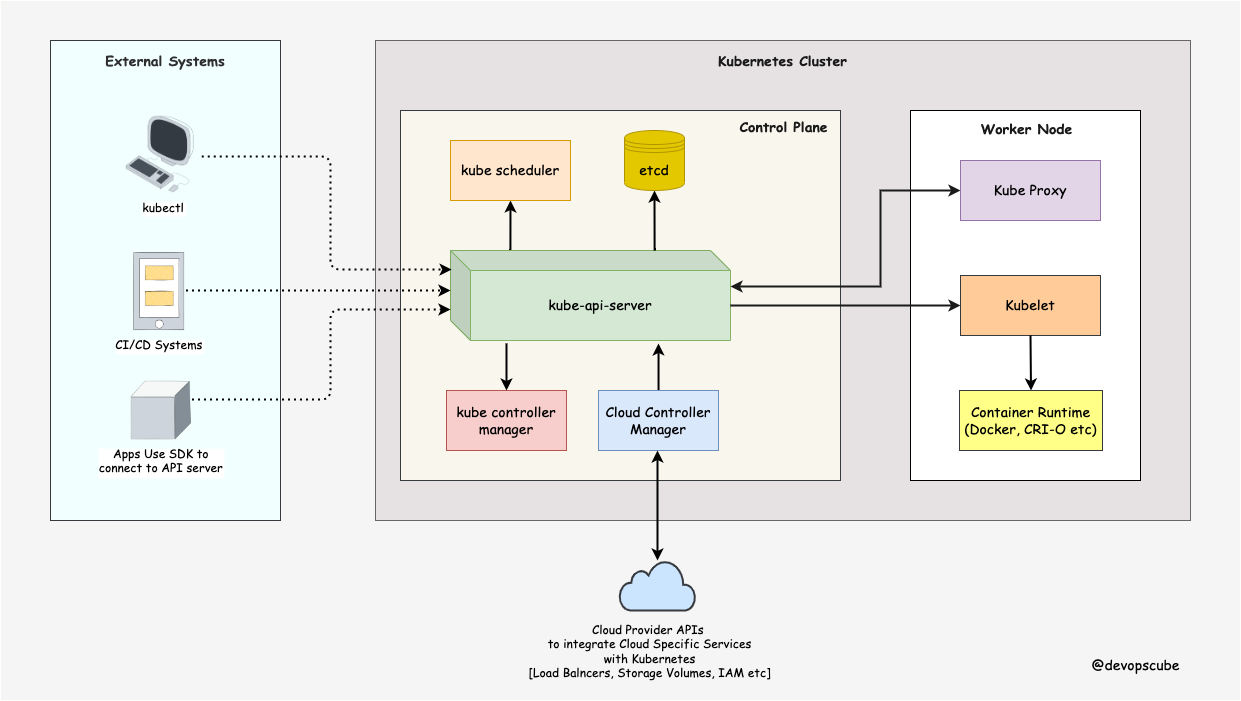
control pannel
kube-apiserver
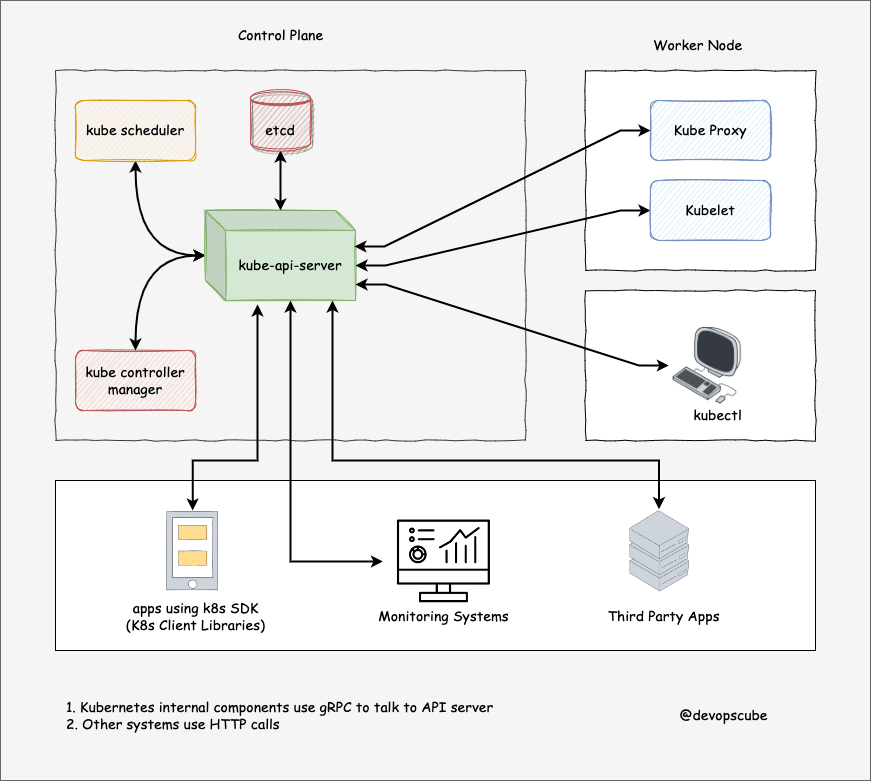
etcd
kube-scheduler
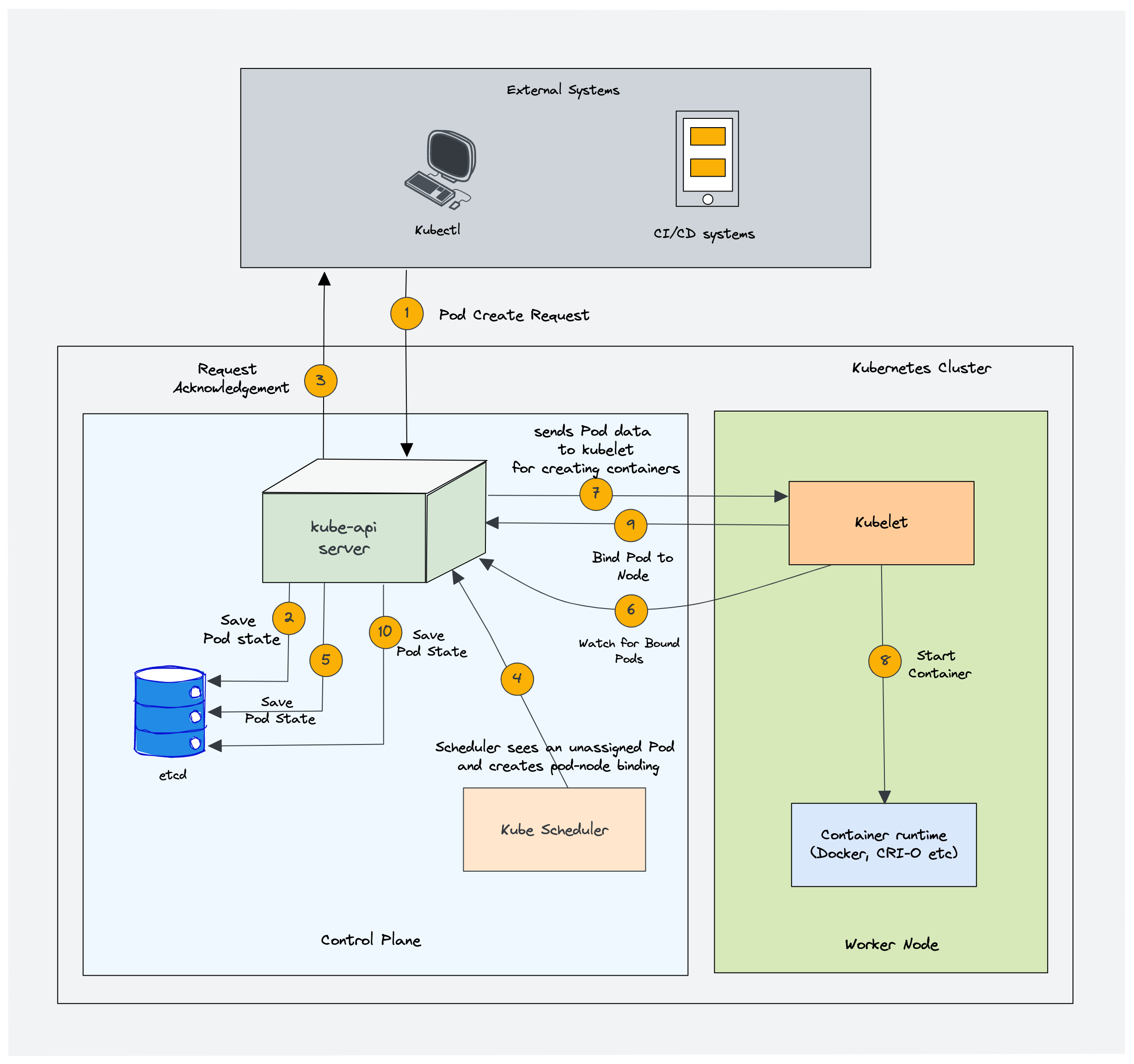
controller manager
ccm : cloud controller manager
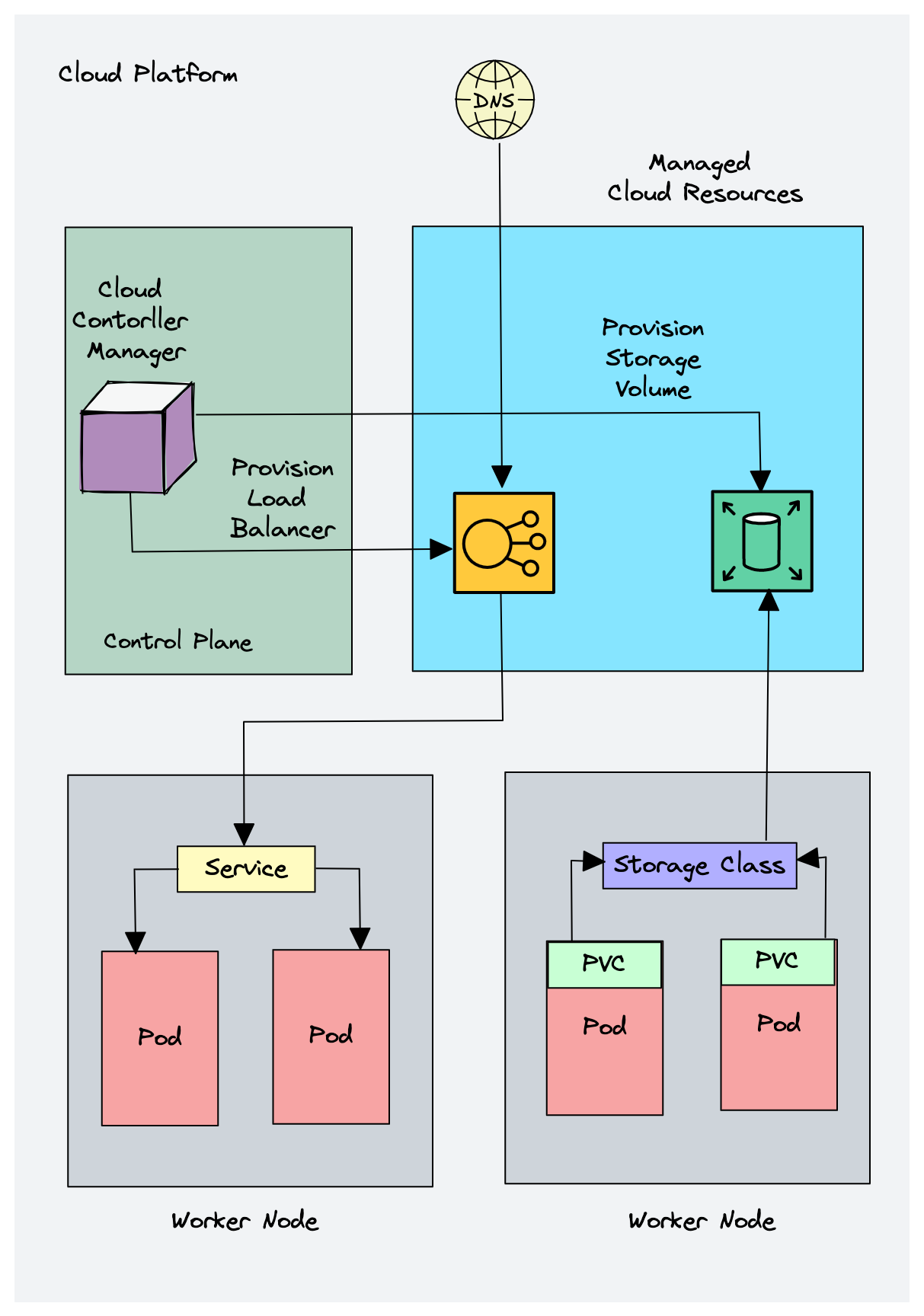
work node
[!NOTE]
- supported endpoints
- linux
RUNTIME PATH TO UNIX DOMAIN SOCKET containerd unix:///var/run/containerd/containerd.sock CRI-O unix:///var/run/crio/crio.sock Docker Engine (using cri-dockerd) unix:///var/run/cri-dockerd.sock
- windows
RUNTIME PATH TO UNIX DOMAIN SOCKET containerd npipe:////./pipe/containerd-containerd Docker Engine (using cri-dockerd) npipe:////./pipe/cri-dockerd
kubelet
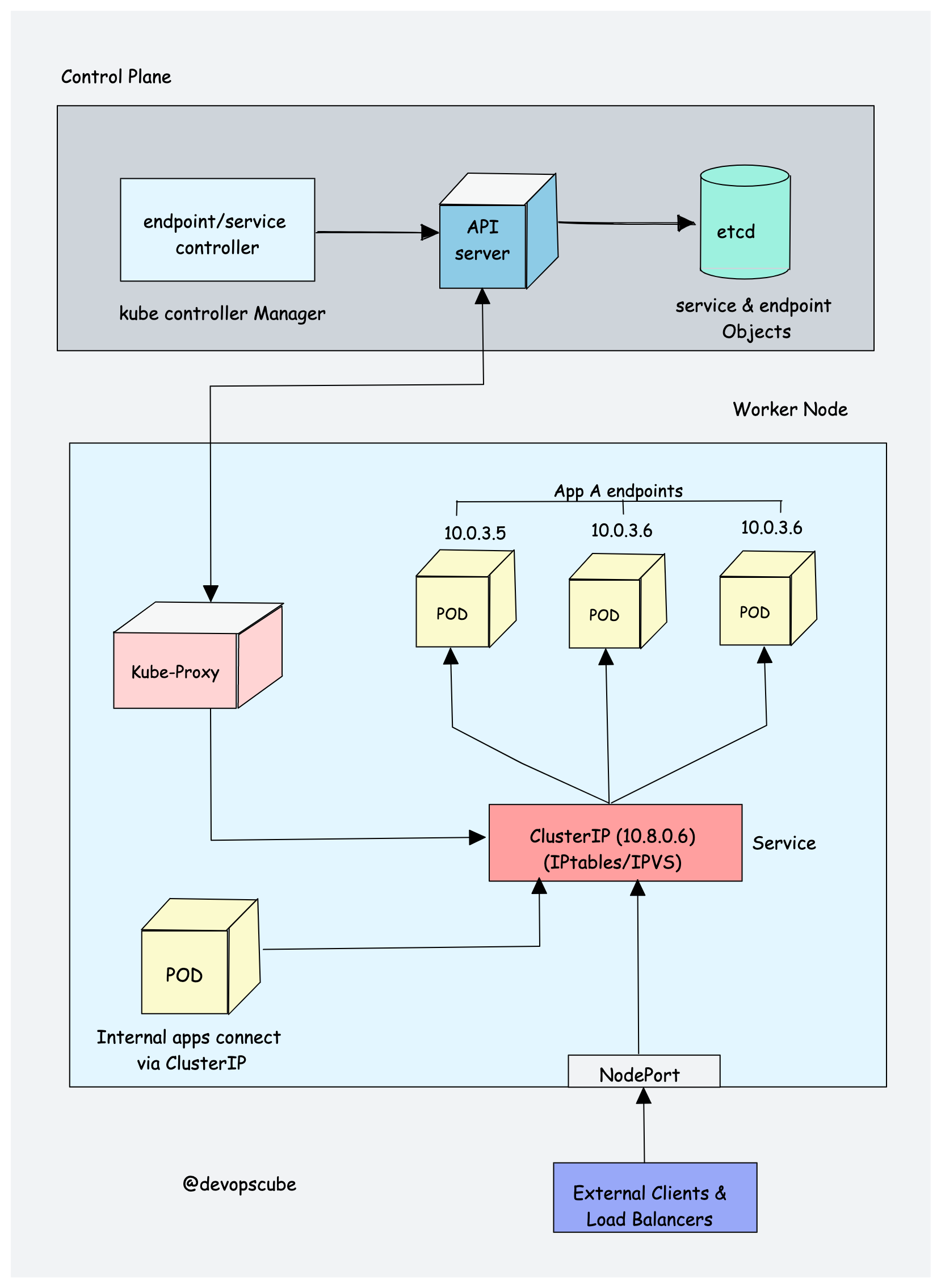
kube proxy
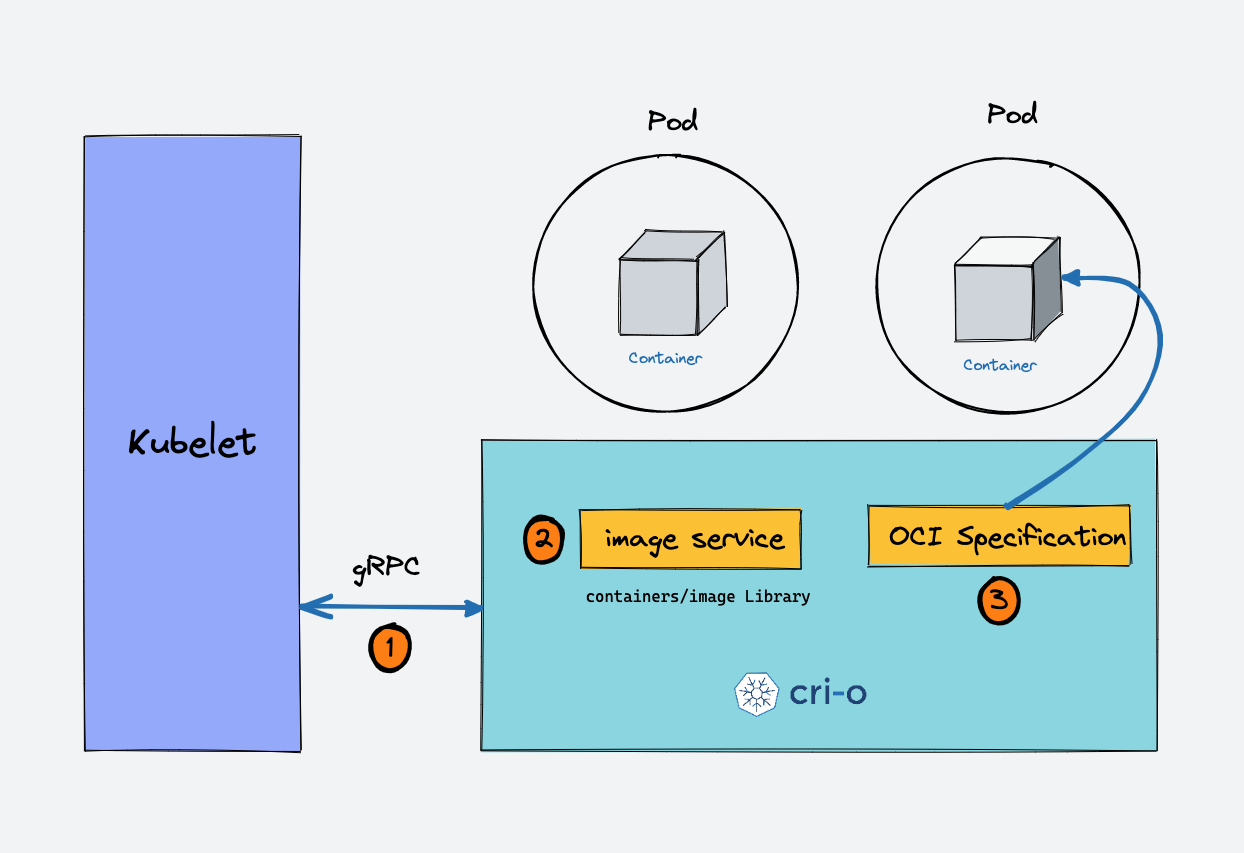
cri-o : container runtime
jsonpath
[!NOTE] references:
options
explain
$ kubectl explain hpa
KIND: HorizontalPodAutoscaler
VERSION: autoscaling/v1
DESCRIPTION:
configuration of a horizontal pod autoscaler.
FIELDS:
apiVersion <string>
...
or
$ kubectl explain configmap KIND: ConfigMap VERSION: v1 DESCRIPTION: ConfigMap holds configuration data for pods to consume. FIELDS: apiVersion <string> APIVersion defines the versioned schema of this representation of an object. Servers should convert recognized schemas to the latest internal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/api-conventions.md#resources ...
kubectl alias
__start_kubectl
$ echo 'source <(kubectl completion bash)' >> ~/.bashrc
$ cat >> ~/.bashrc <<EOF
alias k='kubectl'
alias kc='kubectl -n kube-system'
alias ki='kubectl -n ingress-ngxin'
alias kk='kubectl -n kubernetes-dashboard'
for _i in k kc ki kk; do
complete -F __start_kubectl "${_i}"
done
EOF
$ source ~/.bashrc
_complete_alias
download bash_completion.sh for kubectl
$ curl -fsSL https://raw.githubusercontent.com/cykerway/complete-alias/master/bash_completion.sh > ~/.bash_completion.sh
$ chmod +x !$
$ cat >> ~/.bashrc << EOF
source <(kubectl completion bash)
source ~/.bash_completion.sh
alias k='kubectl'
alias kc='kubectl -n kube-system'
alias ki='kubectl -n ingress-ngxin'
alias kk='kubectl -n kubernetes-dashboard'
while read -r _i; do
complete -F _complete_alias "${_i}"
done < <(sed '/^alias /!d;s/^alias //;s/=.*$//' '~/.bashrc')
EOF
$ source ~/.bashrc
token
check token
$ sudo kubeadm token list
TOKEN TTL EXPIRES USAGES DESCRIPTION EXTRA GROUPS
bop765.brol9nsrw820gmbi <forever> <never> authentication,signing <none> system:bootstrappers:kubeadm:default-node-token
khhfwa.jvkvrpiknx4o6ffy 19h 2018-07-13T11:37:43+08:00 authentication,signing <none> system:bootstrappers:kubeadm:default-node-token
generate token
$ sudo kubeadm token create --print-join-command
kubeadm join 192.168.1.100:6443 --token lhb1ln.oj0fqwgd1yl7l9xp --discovery-token-ca-cert-hash sha256:cba8df87dcb70c83c19af72c02e4886fcc7b0cf05319084751e6ece688443bde
$ sudo kubeadm token create --print-join-command --ttl=0
kubeadm join 192.168.1.100:6443 --token bop765.brol9nsrw820gmbi --discovery-token-ca-cert-hash sha256:c8650c56faf72b8bf71c576f0d13f44c93bea2d21d4329c64bb97cba439af5c3
tear down
[!TIP]
ubuntu
$ kubectl drain <node name> --delete-local-data --force --ignore-daemonsets $ kubectl delete node <node name> $ sudo kubeadm reset [preflight] Running pre-flight checks. [reset] Stopping the kubelet service. [reset] Unmounting mounted directories in "/var/lib/kubelet" [reset] Removing kubernetes-managed containers. [reset] Deleting contents of stateful directories: [/var/lib/kubelet /etc/cni/net.d /var/lib/dockershim /var/run/kubernetes /var/lib/etcd] [reset] Deleting contents of config directories: [/etc/kubernetes/manifests /etc/kubernetes/pki] [reset] Deleting files: [/etc/kubernetes/admin.conf /etc/kubernetes/kubelet.conf /etc/kubernetes/bootstrap-kubelet.conf /etc/kubernetes/controller-manager.conf /etc/kubernetes/scheduler.conf] $ systemctl stop kubelet $ docker system prune -a -f $ systemctl stop docker $ sudo rm -rf /etc/kubernetes/ $ sudo rm -rf /var/lib/cni/ $ sudo rm -rf /var/lib/kubelet/* $ sudo rm -rf /etc/cni/ $ sudo ifconfig cni0 down $ sudo ifconfig flannel.1 down $ rm -rf ~/.kube/ $ sudo apt purge kubeadm kubectl kubelet kubernetes-cni kube* $ sudo apt autoremoveCentOS/RHEL
$ kubectl drain <node name> --delete-local-data --force --ignore-daemonsets $ kubectl delete node <node name> $ sudo kubeadm reset $ docker system prune -a -f $ systemctl stop kubelet $ systemctl disable kubelet $ systemctl stop docker $ systemctl disable docker $ sudo ifconfig cni0 down $ sudo ifconfig flannel.1 down $ sudo ifconfig docker0 down $ sudo yum versionlock delete docker-ce $ sudo yum versionlock delete docker-ce-cli $ sudo yum versionlock delete kubeadm $ sudo yum versionlock delete kubelet $ sudo yum versionlock delete kubectl $ sudo yum versionlock delete kubernetes-cni $ sudo yum remove -y docker-ce docker-ce-cli containerd.io kubectl kubeadm kubelet kubernetes-cni $ sudo yum autormeove $ rm -rf /home/devops/.kube/ $ sudo rm -rf /etc/cni $ sudo rm -rf /etc/kubernetes/ $ sudo rm -rf /etc/docker/ $ sudo rm -rf /etc/systemd/system/multi-user.target.wants/kubelet.service $ sudo rm -rf /etc/systemd/system/multi-user.target.wants/docker.service $ sudo rm -rf /usr/lib/systemd/system/docker.service $ sudo rm -rf /usr/lib/systemd/system/kubelet.service.d/ $ sudo rm -rf /usr/libexec/docker/ $ sudo rm -rf /usr/libexec/kubernetes/ $ sudo rm -rf /var/lib/etcd/ # optional $ sudo rm -rf /var/lib/kubelet/ $ sudo rm -rf /var/lib/dockershim/ $ sudo rm -rf /var/lib/yum/repos/x86_64/7/kubernetes/ $ sudo rm -rf /var/log/pods/ $ sudo rm -rf /var/log/containers/ $ sudo rm -rf /var/run/docker.sock $ sudo rm -rf /var/cache/yum/x86_64/7/kubernetes $ sudo yum clean all $ sudo rm -rf /var/cache/yum $ sudo yum makecache $ sudo yum check-update